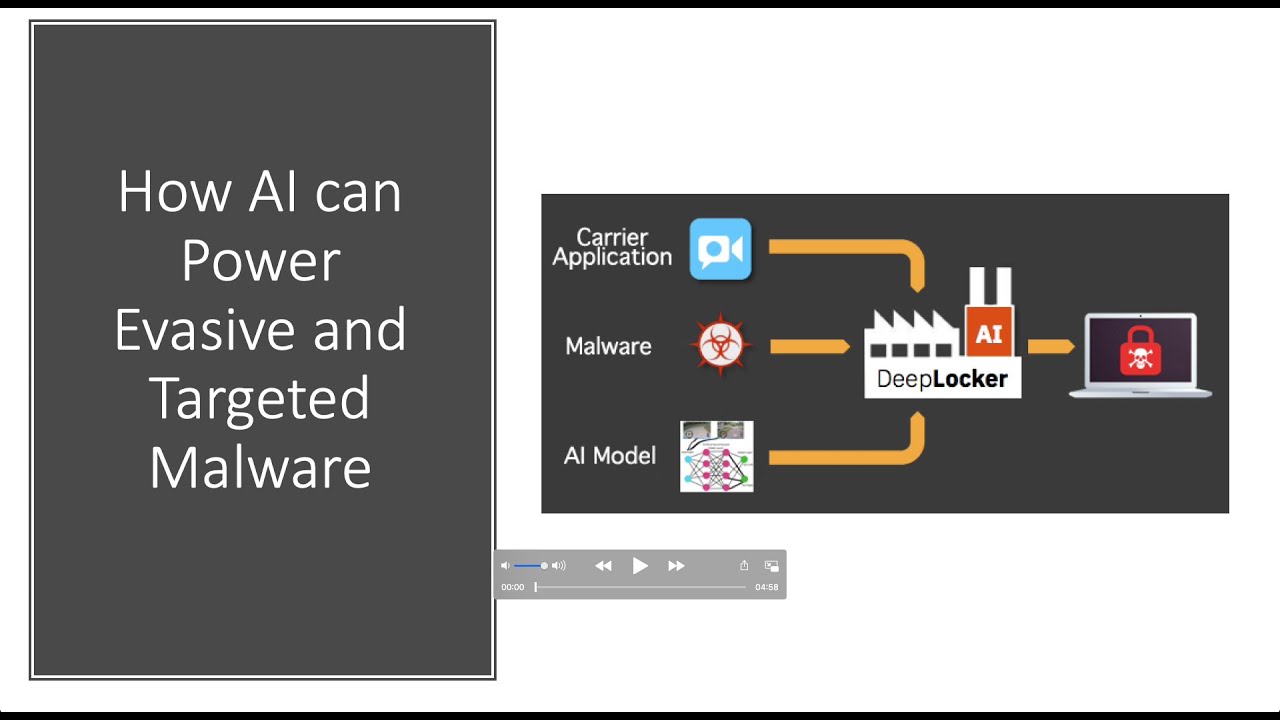
This is the first in a three part series on how next generation malware use AI to enhance their offensive capabilities and are emergent threats. In this post we look at how DeepLocker uses a Neural Network, a benign carrier application and a malicious payload to power evasiveness and targeting.
Over the course of the series we will examine how this new class of malware works in ever increasing detail.
In part two we further analyse DeepLocker and examine a GUI attack and a Neural Network Trojan. While the implementation and functionality of the Neural Network differ in each case, they all have the ability to evade anti-virus and malware scanners. How Artificial Intelligence Can Power Evasive and Targeted Malware Part 2
In part three we create a Windows Application that can evade Windows Defender which includes a Firewall and Norton LifeLock Anti-Virus which includes an Intrusion Prevention System (IPS) on an up to date Windows 10 machine. This application uses a known exploit yet can still run a meterpreter shell on the victim machine and maintain persistence. How Artificial Intelligence Can Power Evasive and Targeted Malware Part 3